at is Data Safety, why is it important, and how do you go about designing into the foundations of your data environment?
When you see the phrase “Data Safety”, the chances are you think of Data Security. Most people do.
What is far less likely is that you think of the other two pillars of Data Safety: Data Privacy and Data Governance.
Clearly, all three pillars overlap. But Data Security seems to attract the most media attention, the most scrutiny and the most attention among business data leadership. In fact, when you compare the worldwide relative volumes of searches for the three terms, it shows an almost spookily even distribution:
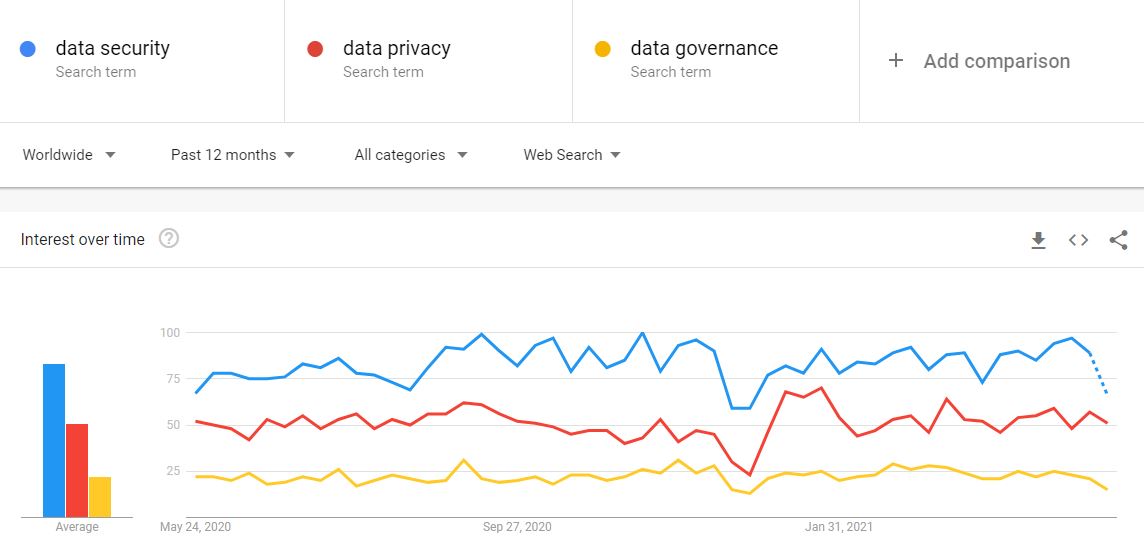
And yet, when you consider the typical data lifecycle, all three pillars have an equally vital role in the protection of data at every single stage.
A simplistic – and by no means exhaustive – example…
| Data Security | Data Privacy | Data Governance | |
| Data is created / received | Threat assessment | Right to Object Right to Rectification Authority to receive | Suitable administration and custodianship |
| Data is hosted | Encryption | Transparent and suitable location | Suitable administration and custodianship Backup and archival |
| Data is processed | Appropriate use Appropriate user | Data subject consent | Industry regulations |
| Data is relocated | Suitable destination | Transparency with data subject Data residency | Suitable destination |
| Data is shared | Appropriate and verified recipient – not a malicious actor | Appropriate and verified recipient – transparency with data subject | Appropriate and verified recipient – industry regulations |
| Data is lost | Duty to report | Duty to report | Backup and disaster recovery |
As has been said about Data Security for decades, the only way to ensure robust and continuous Data Safety with every interaction is to design it into the fabric of your data workflows. It is after all well-known that neither security, privacy nor governance can be applied as afterthoughts – they have to be built into a business’s operations from the ground-up. Every process the data flows through, every person who interacts with it and yes, every technology on its journey.
And there is no technology more crucial to data’s journey through a business than your cloud environment. Your cloud sets the tone for how your data is treated.
How can Data Safety become part of my cloud DNA?
We asked our Chief Information Security Officer, Mark Herridge, for his guidance on how to make sure that your cloud environment sets the right tone for how your data is treated throughout the business.
Data Safety in your cloud environment
| Shift ‘Data Safety’ left | Include security, privacy and governance considerations early into the procurement process versus adding in the final stages of development. |
| Own Your Data | All data requires an owner, so assign owners who understand the datasets, the current and potential value it holds to your business, and who are made responsible for defining each dataset’s data safety requirements. |
| Classify and Tag | Assign a sensitivity hierarchy to all your data, and keep security context with data whenever it moves between systems and services to ensure its Data Safety is maintained. |
| Lifecycle | Set a lifecycle that determines when data can be retired and is no longer needed to help ensure stale data does not linger, increasing your risk profile unnecessarily, and also consuming cost and potentially impacting decisions. |
| Location and Legislation | Know where all your data is stored and why, and the associated local data protection laws |
| Redefine your architecture | Define your architecture around the benefits offered by the cloud. Don’t redeploy the same architecture you use in your legacy environments in the cloud – especially as your previous Data Safety measures are either inappropriate to the cloud or outdated. |
| Control Alignment | Check the alignment between your and your cloud provider’s security controls and where responsibilities lie. Identify and address any gaps. |
| Monitor and Manage Vendor Risk | Ensure the provider complies with relevant regulations and you proactively monitor the service. Identify any sub-services the provider uses. Review the provider’s third-party audits. |
“Data safety really does entail security, privacy and governance. They go hand-in-hand, you can’t focus fully on one, and not the others – they are both supportive of and reliant on each other.”
Mark Herridge
Chief Information Security Officer, Calligo
The two key takeaways are simple: Data Safety must not be treated as synonymous with Data Security, and the entirety of Data Safety must be written into the fundamentals not only of your cloud environment’s design, but also how data is interacted with from it.
To find out more about data safety and the commercial benefits it can deliver to your organization.



 Back
Back